How do I connect AWS to Opscompass for the first time?
Opscompass makes it easy to connect AWS with Opscompass for the first time. Follow these steps to connect.
First Time Setup
This article will explain the AWS account connection process for those connecting AWS to Opscompass for the first time.
AWS Organizations
- Accounts joined with Opscompass must be a member of an AWS organization.
Verifying an Organization within the AWS console:
From the AWS console home dashboard, type or navigate to "AWS Organizations."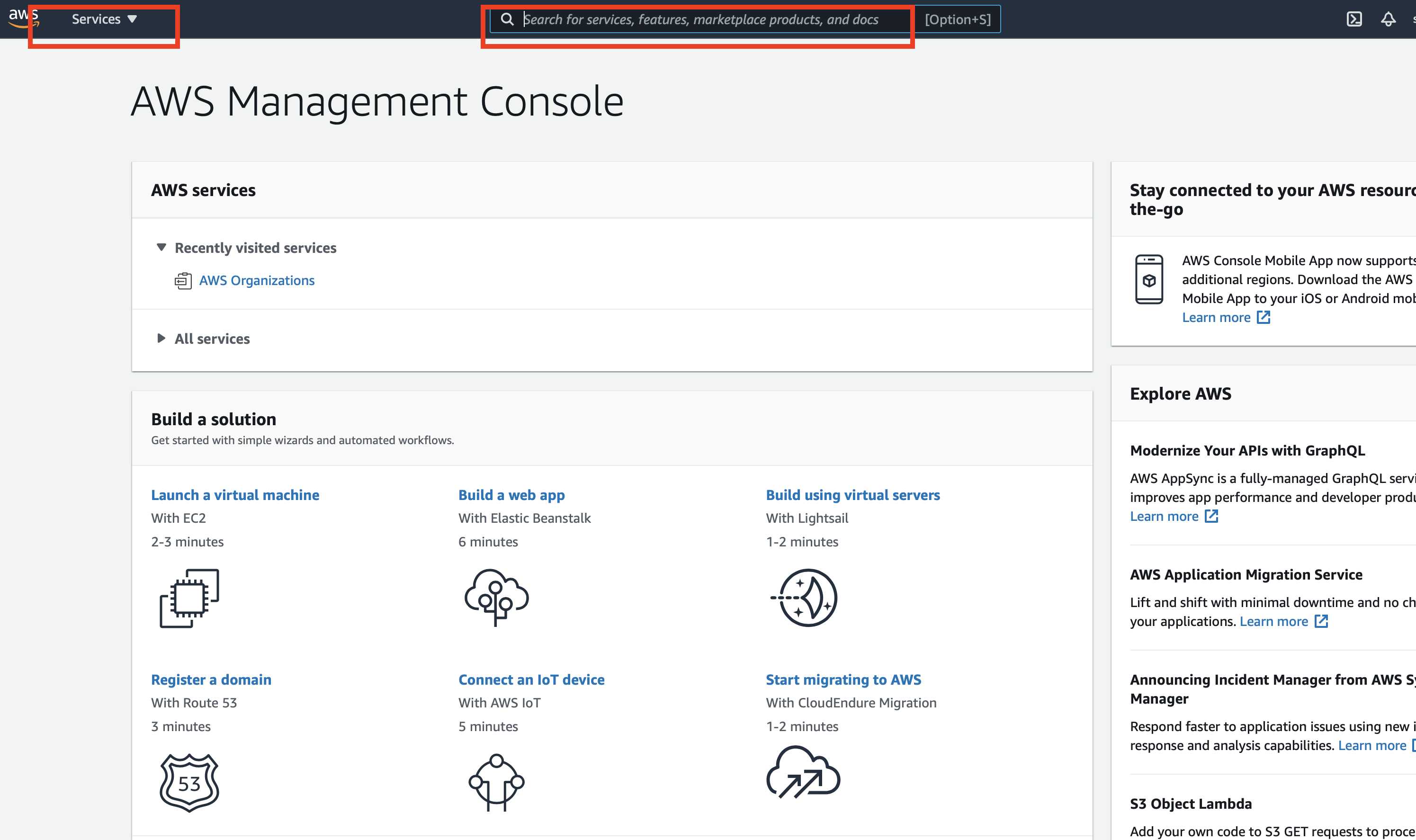
You can verify whether you are a part of an organization here. If you are not a part of an organization and don't see a similar screen in AWS, please continue to step C.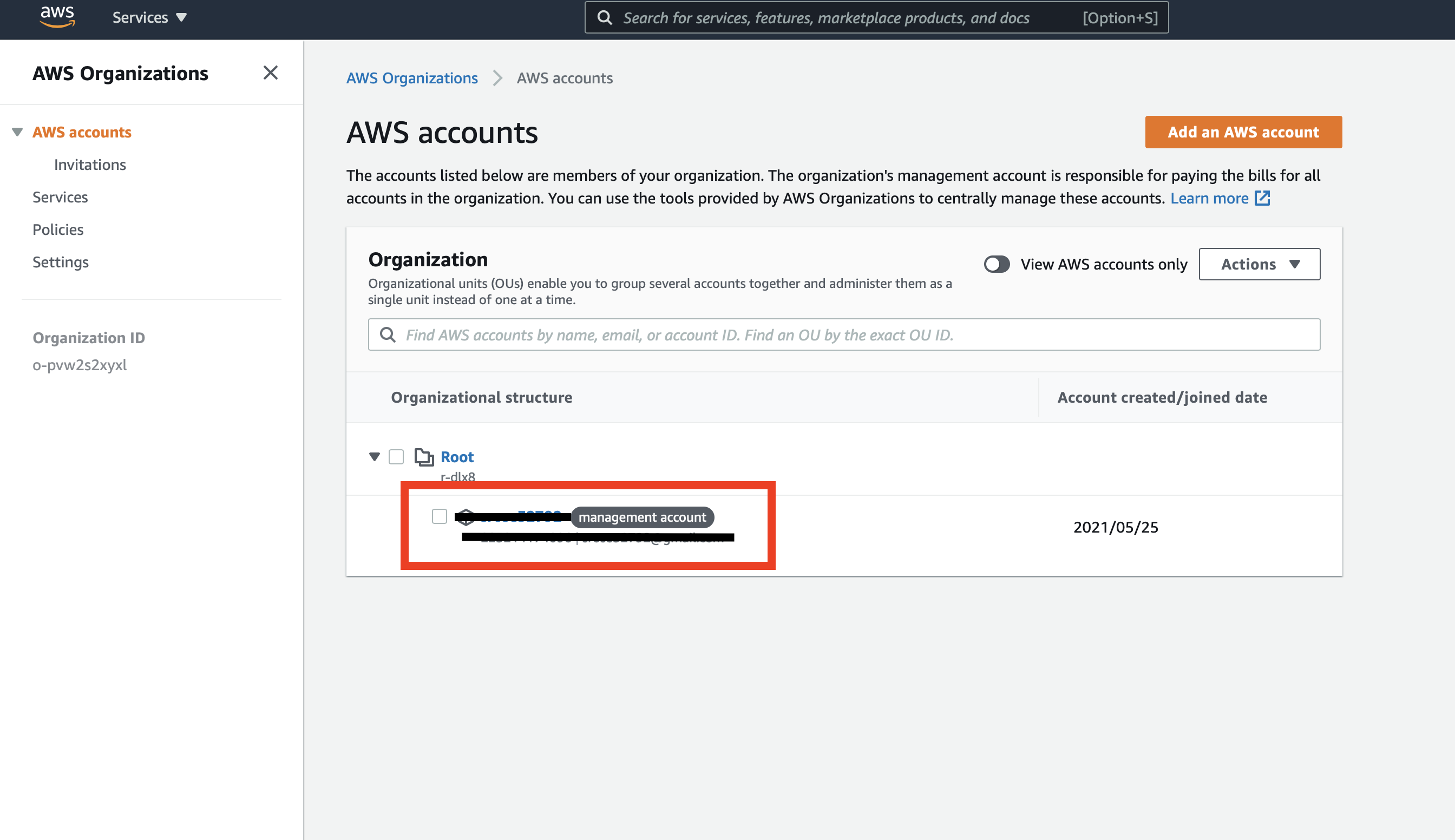
Click on "Create an organization". You can also see "Get Started with AWS Organizations".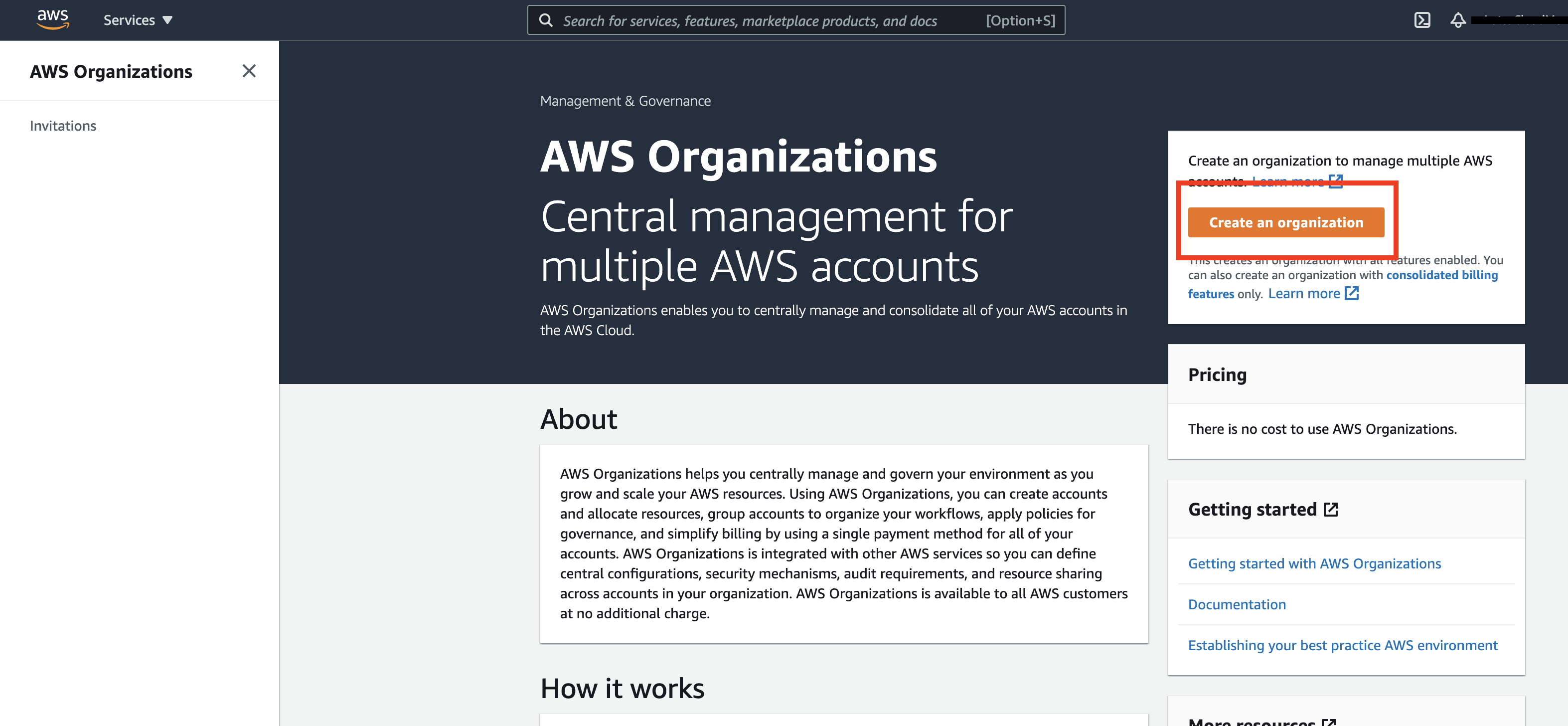
Opscompass uses a read-only access role that exists in your AWS IAM service. This role provides the necessary permissions for Opscompass to scan resources, detect events and report those to the Opscompass platform. There are two ways to create the AWS IAM Role appropriate for Opscompass, the AWS Console, and the AWS Command Line Interface (CLI).
Creating AWS IAM Roles using the AWS Console
- Log into the AWS Console.
- Click the link to deploy the Opscompass Viewer IAM Role. This takes you to the CloudFormation Portal and sets all required fields as they are expected for Opscompass.
- Stack Name – Changing the supplied value will cause the connection to fail.
- External ID - The external ID can be changed if needed.
- Acknowledge the warning about IAM resources with custom names.
- Click the link to deploy the Opscompass Viewer IAM Role. This takes you to the CloudFormation Portal and sets all required fields as they are expected for Opscompass.
- Click ‘Create Stack.’
- This creates the Opscompass viewer role with necessary permissions
- A new IAM policy, Opscompass Denial role denies Opscompass access to contents of S3 objects, databases, and other resources.
- A new IAM policy for Opscompass denial is created, which is associated to the Denial role.
- Navigate to the newly created role in the AWS IAM Portal.
- Copy the role ARN to the clipboard.
- Return to Opscompass. In Opscompass, two edit fields appear:
- AWS External ID – This is a generated field. If this field is changed, the Opscompass Viewer role needs to be updated to match the new value.
- Role ARN – Past the ARN of the newly created Opscompass View IAM Role. This must match the AWS IAM View Role ARN to successfully connect.
- Click Connect. Upon connection, Opscompass displays a progress bar to the user, indicating the status of account connection. Error messages will be displayed to the user in the case of problems. The process for connecting an account includes:
- Verifying the selected Role is a member of an organization.
- Verifying the role exists and has the correct permissions.
- Connect to the account and create the Opscompass tenant for this account.
- Attempt to scan resources for the accounts in the organization, using the created role.
- After the verification is complete, Opscompass begins scanning resources in the account you have connected. This may take several minutes to complete if the account contains a large number of resources.
NOTE: If you click “skip” and proceed to the product dashboard, you may not immediately see all the resources that you are expecting. It may take several minutes for all resources to appear.
Creating AWS IAM Roles using the AWS CLI
Rather than using the AWS Console, you can create the Opscompass IAM roles using the AWS CLI.
- Using the AWS Command Line Interface (CLI) – Opscompass has introduced new CLI commands to help you simplify the account connection process. Select “Setup our account via command line interface” in the Account Connection page.
- Verify that your AWS CLI ins installed an associated to the account you wish to connect, using the command:
aws --version
- You can deploy the Opscompass Integration CloudFormation Template by copying the command and executing it in the AWS CLI.
aws cloudformation create-stack --stack-name OpscompassIntegration --template-url https://Opscompass-templates.s3.amazonaws.com/Opscompass_role_creation.template --capabilities CAPABILITY_NAMED_IAM --parameters ParameterKey=ExternalID,ParameterValue=[this will be provided during setup] && aws cloudformation wait stack-create-complete --stack-name OpscompassIntegration
- After the command has executed successfully, you can verify the existence of the Opscompass Viewer role:
aws iam get-role --role-name OpscompassViewer
- After completing the Opscompass Integration CloudFormation Template deployment, copy the resource ID (the AWS ARN) to the clipboard, and proceed with the connection experience.
- Paste the ARN into the Role ARN field.
- Click Connect. Upon connection, Opscompass displays a progress bar to the user, indicating the status of account connection. Error messages will be displayed to the user in the case of problems. The process for connecting an account includes:
- Verifying the selected Role is a member of an organization.
- Verifying the role exists and has the correct permissions.
- Connect to the account and create the Opscompass tenant for this account.
- Attempt to scan resources for the accounts in the organization, using the created role.
- After the verification is complete, Opscompass begins scanning resources in the account you have connected. This may take several minutes to complete if the account contains a large number of resources.
- If you click “skip” and proceed to the product dashboard, you may not immediately see all the resources that you are expecting. It may take several minutes for all resources to appear.
Adding Event Forwarding to Opscompass Using the AWS Console
- Creating the Event Forwarding architecture – Opscompass supports the forwarding of CloudTrail events from AWS accounts, allowing for near real time resource scanning and analysis for supported events. There are two ways to create the AWS Event Forwarding architecture appropriate for Opscompass.
- Be sure you are logged into the AWS Console.
- Return to Opscompass
- Click the ‘Enable Event Scanning’ button to deploy the Opscompass EventForwarding Template. This takes you to the CloudFormation Portal and sets all required fields as they are expected for Opscompass.
- Stack Name – Changing the supplied value will cause the connection to fail.
- Click ‘Create Stack.’ This begins the deployment of the following resources
- An event forwarding rule, used to select and send CloudTrail events to Opscompass.
- A CloudTrail to capture events generated by CloudTrail and AWS services.
- A S3 Bucket, used to store all events captured by the newly made CloudTrail bucket.
- A S3 Bucket Policy to be attached to the newly created bucket. This allows for the newly created CloudTrail to forward to the S3 bucket.
- Copy the role ARN to the clipboard.
- Once the deployment of the stack is complete, your AWS account is setup to forward events to Opscompass.
- Navigate back to Opscompass
- In Opscompass, click ‘Done’ to be navigated back to your company dashboard.
Using the AWS Command Line Interface (CLI)
- Opscompass has introduced new CLI commands to help you simplify the setup of event forwarding
- Select “Enable event scanning via AWS command line interface”
- You can deploy the OpscompassEventForwarding Template by copying the command and executing it in the AWS CLI
aws cloudformation create-stack --stack-name OpscompassEventForwarding --template-url https://Opscompass-templates.s3.amazonaws.com/Opscompass_event_based.template && aws cloudformation wait stack-create-complete --stack-name OpscompassEventForwarding
- Once the deployment of the stack is complete, your AWS account is setup to forward events to Opscompass.
-
- Navigate back to Opscompass
- In Opscompass, click ‘Skip’ to be navigated back to your company dashboard.
Additional Resources:
How do I connect additional clouds to Opscompass?
How do I connect an Azure account to Opscompass?
How do I connect a Google Cloud (GCP) Project to Opscompass?